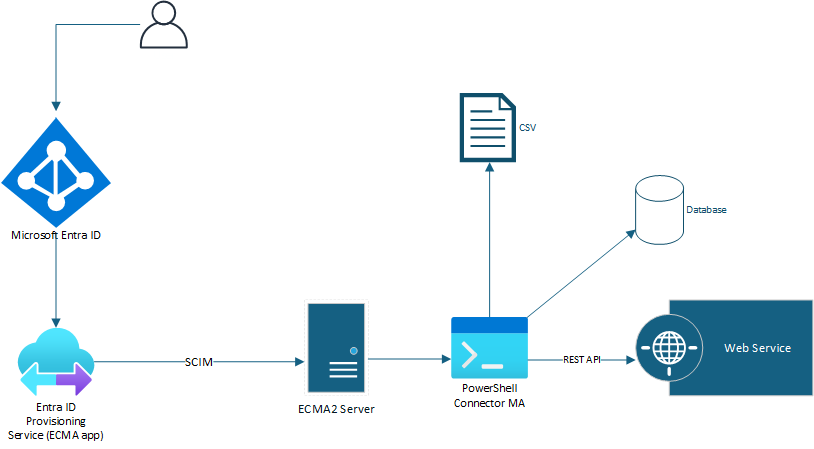
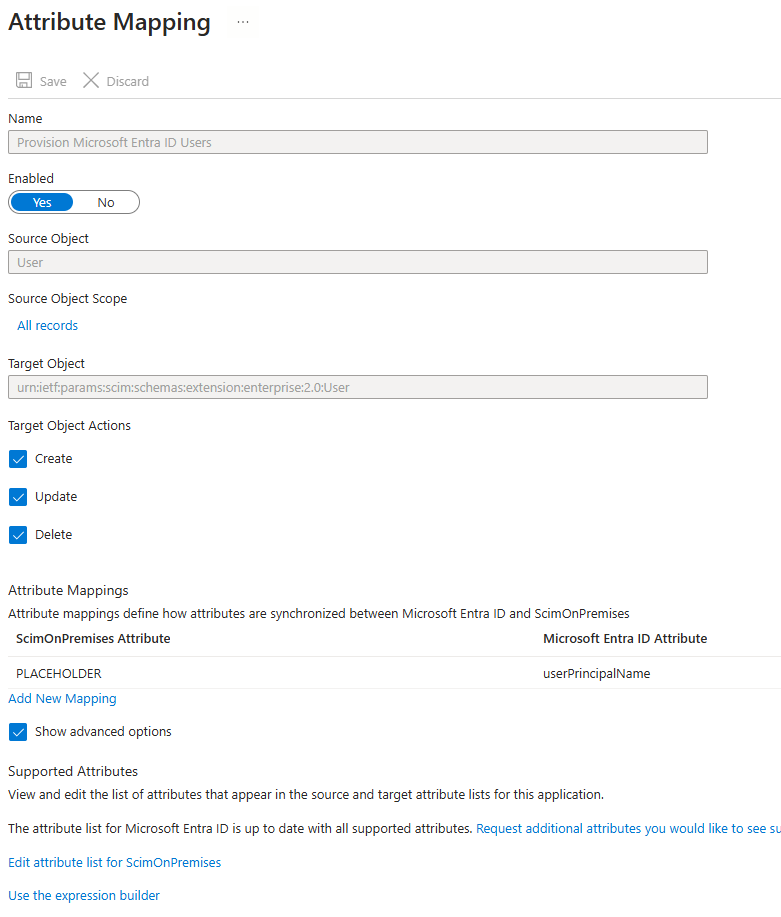
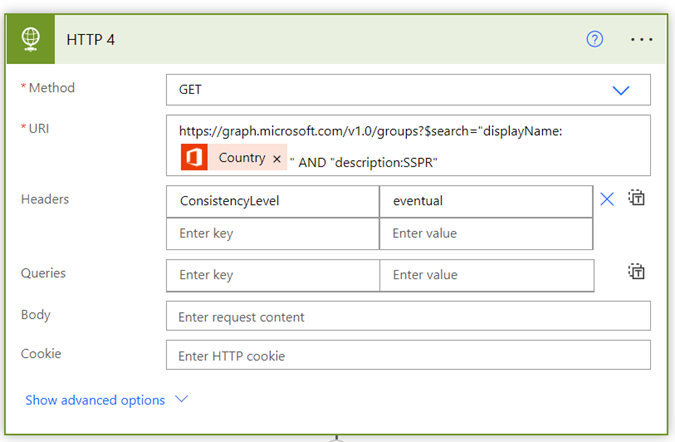
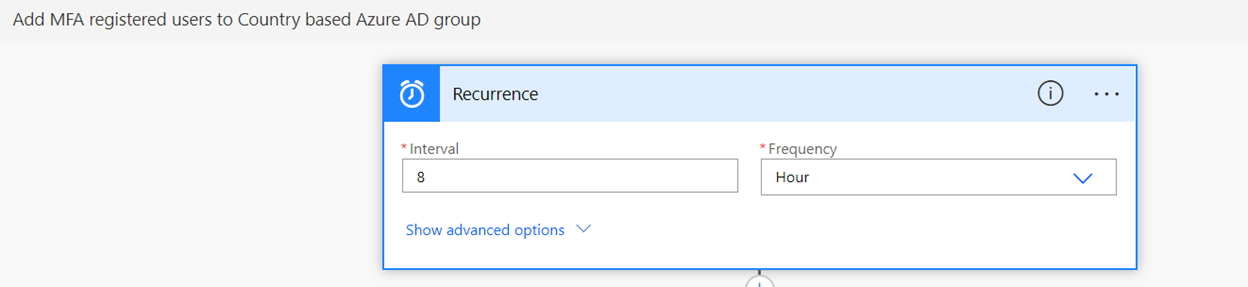
This article covers Windows 10/11 Intune managed devices. To automate device wipe based on Last Checked-In Date and Device Scope Tag using Azure Automation Runbook and Azure Storage Blob for logging.
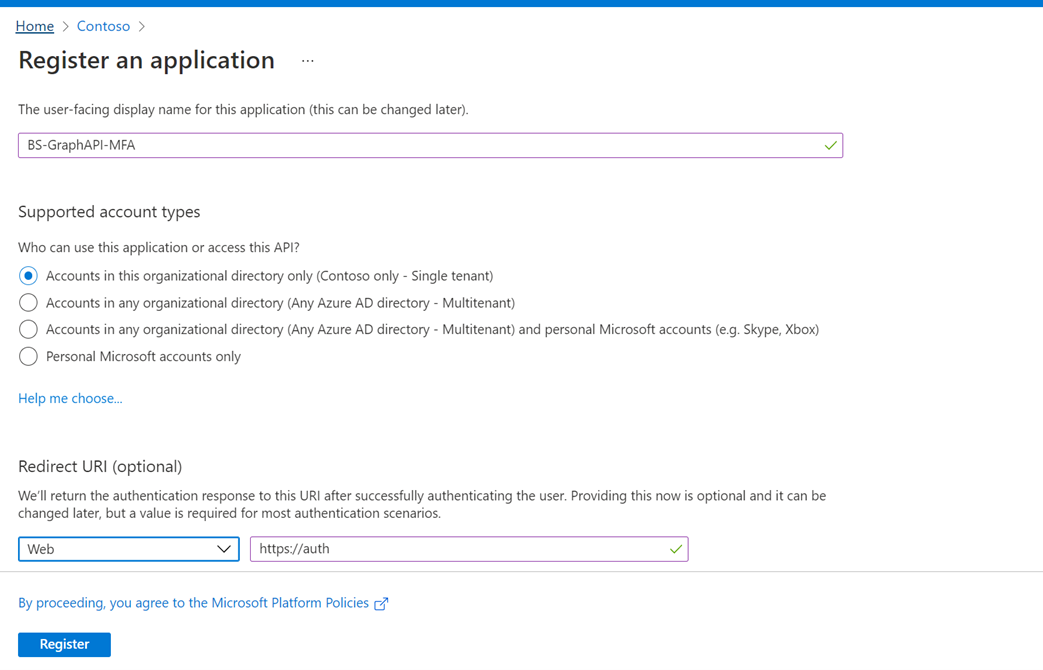
Create Automation Account
- Login to Azure Portal with Administrative or equivalent rights
Then click on the “Automation Accounts”
- Click “Create” and enter appropriate information, then click “Review+Create”
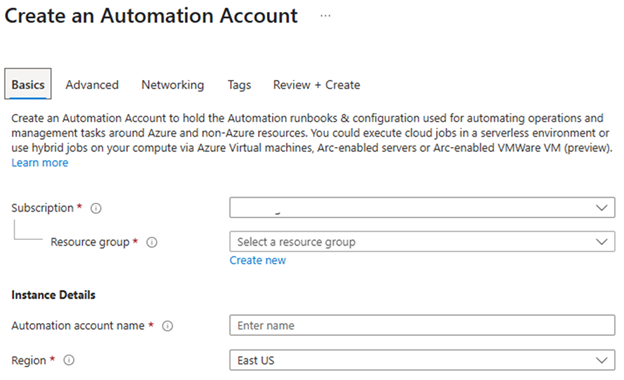
Automation account name (example: IntuneDeviceLifeCycleManagement) - Go to the resource once created then click “Shared Resources -> Modules”
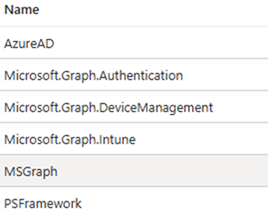
Then browse and add the following modules (Runtime 5.1)
- Under the “Account Settings” of the Automation Account click on “Identity” make a note of the “Object (principal) ID” then use the following PowerShell script to assign API Permissions.
Prerequisites for PowerShell.
Install-Module MSGraph
Use Azure administrative or equivalent account to Authenticate when running the script.
# Connect to Microsoft Graph with required scopes
Connect-MgGraph -Scopes "Application.ReadWrite.All", "AppRoleAssignment.ReadWrite.All" -TenantId "YOUR-TENANT-ID"
# Variables
$managedIdentityObjectId = "Object (principal) ID"
$graphSp = Get-MgServicePrincipal -Filter "AppId eq '00000003-0000-0000-c000-000000000000'" # Microsoft Graph SP
# List of AppRoleIds to assign
$appRoleIds = @(
"dc377aa6-52d8-4e23-b271-2a7ae04cedf3", # DeviceManagementConfiguration.Read.All
"9241abd9-d0e6-425a-bd4f-47ba86e767a4", # DeviceManagementConfiguration.ReadWrite.All
"5b07b0dd-2377-4e44-a38d-703f09a0dc3c", # DeviceManagementManagedDevices.PrivilegedOperations.All
"2f51be20-0bb4-4fed-bf7b-db946066c75e", # DeviceManagementManagedDevices.Read.All
"243333ab-4d21-40cb-a475-36241daa0842", # DeviceManagementManagedDevices.ReadWrite.All
"40dc41bc-0f7e-42ff-89bd-d9516947e474" #
)
# Assign each role
foreach ($roleId in $appRoleIds) {
New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $managedIdentityObjectId `
-PrincipalId $managedIdentityObjectId `
-ResourceId $graphSp.Id `
-AppRoleId $roleId
}
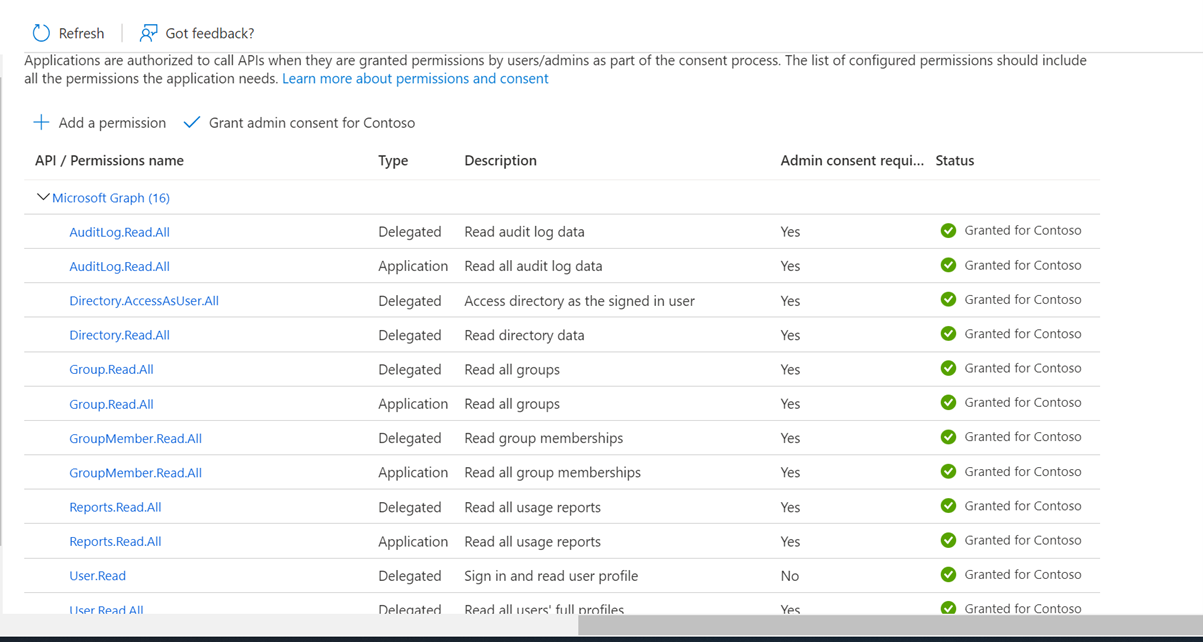
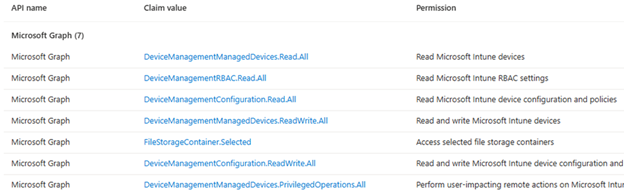
Validate the permissions are assigned to the Managed Identity. From Entra ID portal select Enterprise Application then search by Object ID and view permission.
Create Storage Account
- Create Azure Storage Account

Click “Create” and enter the required information. Then click “Review+Create”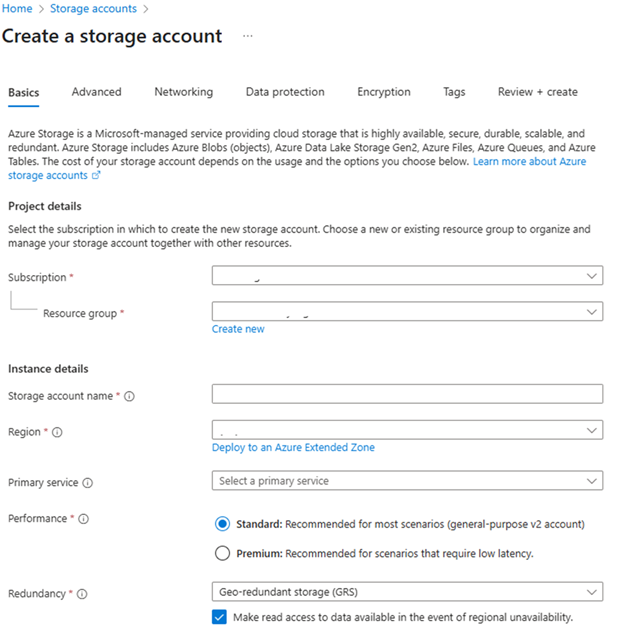
- Access the Storage Account and create a “+Container”
- Access the Container and click on “Access Control (IAM)”
- Assign permissions to the Container for Managed Identity Automation Account using “Object (principal) ID”
“Storage Blob Data Contributor” and “Storage Blob Data Reader”
Create Runbook
- From the Automation Account under Process Automation select Runbooks then “+Create a runbook”
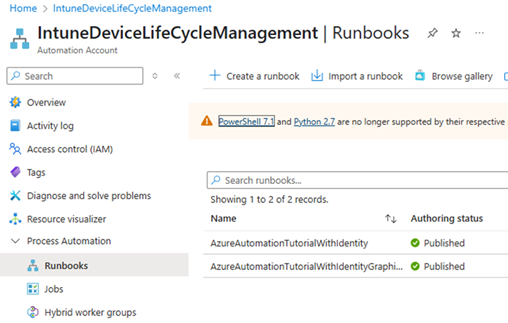
- Select the following to create the Runbook then click “Review + Create”
- Use Edit in Portal option to copy the following script.
Replace the following items with your environment values.
• $daysInactive = 10
• $targetScopeTagName
• $logFileName
• $emailRecipient
• $emailSender
• $smtpServer
• AUTOMATION-ACCOUNT-MANAGED-IDENTITY-OBJECT-ID
• $storageAccountName
• $containerName
• YOUR-STORAGE-CONNECTION-STRING
# Purpose of Sample Scripts:
# Microsoft provides sample scripts to demonstrate functionality or provide solutions to specific problems. These scripts are intended to b
e examples and may not be suitable for all environments or situations.
# Not Supported" Disclaimer:
# The disclaimer signifies that Microsoft doesn't offer formal support for these scripts. This means they won't provide bug fixes, troubleshooting, or customization assistance for the script.
# "AS IS" Provision:
# The "AS IS" clause means the scripts are provided in their current state without any guarantee of functionality, accuracy, or suitability for a particular purpose.
# Define parameters
# Change the default values
param (
[int]$daysInactive = 10,
[string]$targetScopeTagName = "YOUR-DEVICE-SCOPE-TAG",
[string]$logFileName = "WipedDevicesLog",
[string]$emailRecipient = "YOUR-RECIPIENT-EMAIL",
[string]$emailSender = "YOUR-SENDER-EMAIL"
)
# Set the cut of date
$cutoffDate = (Get-Date).ToUniversalTime().AddDays(-$daysInactive).ToString("yyyy-MM-ddTHH:mm:ssZ")
# Connect to Intune
# Connect-MSGraph
# Connect to MSGraph
Write-Output "`n+ Connecting to Graph (Managed Identity)"
Connect-MgGraph -Identity -ClientId "AUTOMATION-ACCOUNT-MANAGED-IDENTITY-OBJECT-ID"
# Initialize log content
$logContent = "Wiped Devices Log - $(Get-Date)`n`n"
# Set the scope ID filtering on
$targetScopeTagId = $null
# Get all available scope tags and find the ID of the one you want
$scopeTags = Invoke-MgGraphRequest -Method GET -Uri "https://graph.microsoft.com/beta/deviceManagement/roleScopeTags"
$targetScopeTagId = ($scopeTags.value | Where-Object { $_.displayName -eq $targetScopeTagName }).id
if (-not $targetScopeTagId) {
Write-Error "Scope tag '$targetScopeTagName' not found!"
return
}
# Get all managed devices (you can paginate here if needed)
$allDevices = Get-MgDeviceManagementManagedDevice -Filter "lastSyncDateTime lt $cutoffDate" | Select-Object Id, DeviceName, LastSyncDateTime, OperatingSystem
# Prepare output array
$matchingDevices = @()
# Get devices that have not checked in for the specified number of days
Write-Output "`n+ Getting Devices from Intune"
# Loop through each device to retrieve its roleScopeTagIds
foreach ($device in $allDevices) {
$deviceDetails = Invoke-MgGraphRequest -Method GET -Uri "https://graph.microsoft.com/beta/deviceManagement/managedDevices/$($device.Id)?`$select=id,deviceName,roleScopeTagIds,lastSyncDateTime"
Write-Output "Device Name: $($deviceDetails.deviceName), Device ID: $($deviceDetails.id), Last Check-in: $($deviceDetails.lastSyncDateTime)"
if ($deviceDetails.roleScopeTagIds -contains $targetScopeTagId) {
$matchingDevices += [PSCustomObject]@{
DeviceName = $deviceDetails.deviceName
DeviceId = $deviceDetails.id
LastSync = $deviceDetails.lastSyncDateTime
OperatingSystem = $deviceDetails.OperatingSystem
ScopeTagIds = ($deviceDetails.roleScopeTagIds -join ", ")
}
# Graph endpoint to wipe a device
$params = @{
keepEnrollmentData = $true
keepUserData = $true
}
# Device Wipe Call
Clear-MgDeviceManagementManagedDevice -ManagedDeviceId $device.Id -BodyParameter $params
$logContent += "Device Name: $($deviceDetails.deviceName), Device ID: $($deviceDetails.id), Last Check-in: $($deviceDetails.lastSyncDateTime)`n"
}
}
# Output the matching devices
$matchingDevices | Format-Table
# Write log to storage
# set storage account details
$storageAccountName = "YOUR-STORAGE-ACCOUNT-NAME"
$containerName = "YOUR-STORAGE-CONTAINER-NAME"
$blobName = "$logFileName-$(Get-Date -Format 'yyyyMMdd-HHmmss').txt"
$storageContext = New-AzStorageContext -ConnectionString "YOUR-STORAGE-CONNECTION-STRING"
# Create blob from log content
Set-Content -Path "$env:TEMP\$blobName" -Value $logContent
Set-AzStorageBlobContent -File "$env:TEMP\$blobName" `
-Container $containerName `
-Blob $blobName `
-Context $storageContext `
-Force
# Clean up temp file
Remove-Item "$env:TEMP\$blobName"
# TODO: Send email to required party.
Validation
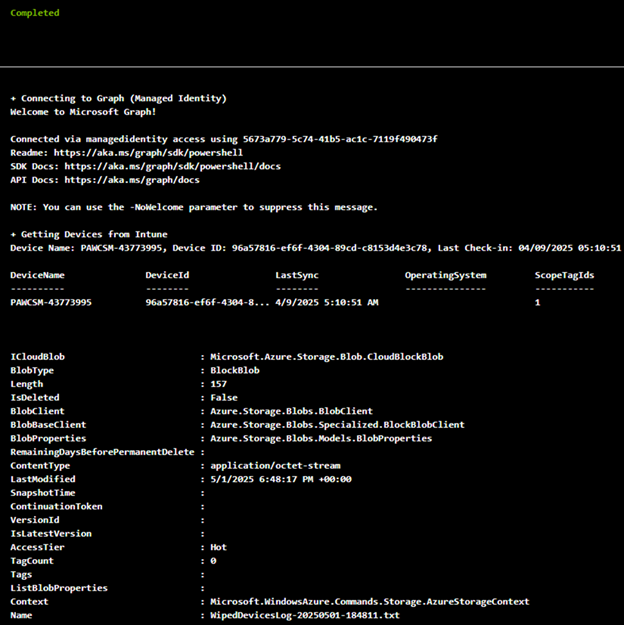
- Click the “Test pane”
- Click the “Start” button
- Ensure the task is completed without any errors, similar to the example below then close the window “X” button.
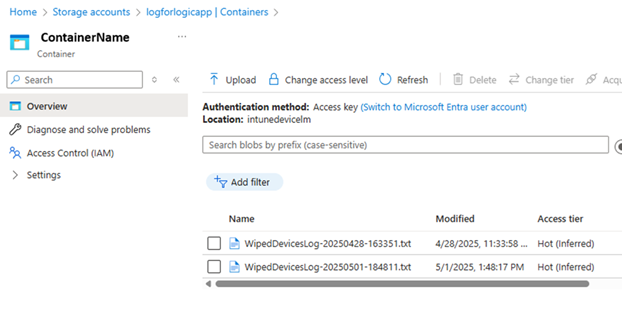
- Validate the storage container to ensure logs were generated
Publish
- Click the “Publish” button, then click “Yes” button.